Accellera adds detail to proposed security assurance model
An Accellera group with the task of finding a way for IP-core providers to give their customers details on how they have secured their designs has released a white paper setting out their initial plans.
Although the problem of dealing with the unknown unknowns of security remains open, the aim of the IP Security Assurance (IPSA) standard is to attack the known knowns and known unknowns with a database of vulnerabilities and the countermeasures applied.
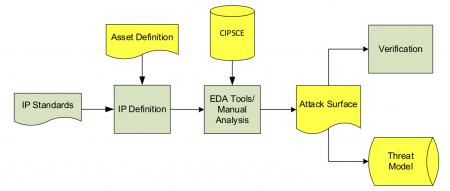
The proposal from the IPSA group is to add three components to an IP core’s delivery collateral: asset definition; attack surface; and threat model informed by a knowledge base called the Common IP Security Concerns Enumeration (CIPSCE). An early example of what is likely to go into that knowledge is in the white paper.
The reason for those three pieces of collateral is that it is practically impossible, at least with today's methods, to secure a core or a design without an understanding of the likely threats and the attack surface it presents. Mostly, these will be I/Os and the standard calls for these top-level ports to be declared in the standard. However, for highly sensitive cores such as cryptoprocessors, we can probably expect side-channel attack vectors to be included as well.
Image Conceptual workflow envisaged by IPSA
According to the group, the CIPSCE database will provide a standard nomenclature and cataloging of common security concerns to help simplify and classify the appropriate weaknesses. The goal is to have Accellera host a public database that will support field queries and downloads for scalability. The content will be controlled by Accellera, but the community will be able to submit entries to the IPSA working group for review and approval.
The white paper includes a model of how the working group expects IP suppliers to provide security information. The example is an OpenCore OR1200 processor, which for the purposes of the proposed framework, comprises a collection of assets. “An asset can be identified as a port, module, register, combination, and so on,” the authors write. “Each asset will have its own asset attribute table.“
The working group expects tool suppliers will create software that parses the attribute tables and builds up attack surfaces and threat models that can then be used during testing and verification by the IP integrator. Alternatively, integrators will build their own attacks and tests based on the tables. As the work continues, the working group is coordinating community input at an Accellera online forum.