Cybersecurity must be built in not bolted on
Cybersecurity rose still further up the agenda during the Covid-19 pandemic. Companies of all types were forced to address endpoint protection in the context of the shift to more work-from-home (WFH), a shift that is unlikely to be entirely reversed. Meanwhile, high profile attacks such as SolarWinds and Log4j have exposed the potential vulnerabilities in software supply chains.
As a result, customers increasingly require that vendors set out their overarching security strategies in terms of how they develop products, and how they address issues around client data and IP protection within them. They don’t want to know everything, but they do want to know that the issue is taken sufficiently seriously. Given the sensitivity and value of the data involved, tools used in electronic systems design are hardly an exception.
Siemens EDA discusses its overarching cybersecurity strategy in a new article, ‘Modern day security practices safeguard a digital transformation’, which describes the company’s internal approach as well as its take on customer data and access. It also provides links to separate resources such as the Siemens Trust Center and Siemens ProductCERT sites that support the strategy.
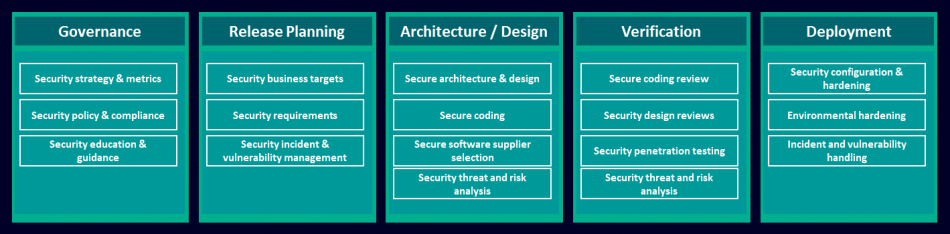
Authors Matt Walsh and Geoff Babb seek to both inform customers and offer Siemens’ strategy as a “starting point” for more comprehensive cybersecurity discussions. At the heart of the paper is an emphasis on treating security as an element that needs to be built-in rather than bolted-on – an approach that they argue should apply to any project.
Figure 1 shows an overview of Siemens’ approach. A key takeaway is that security must be considered before development starts, reviewing repeatedly during the design process and with a close eye on third-party components that are integrated into any products.