Fighting the war of escalation in embedded systems security
Security involves trading off the cost of securing something with the value that is being protected. As our lives move online, the variety of devices that can expose us to significant losses is rising steadily as hackers learn how to exploit security flaws in everything from nannycams to network routers to access valuable data – such as personal information and online identities.
The challenge for designers, therefore, is to find ways of providing high levels of security in low-cost devices that, in themselves, are not worth a hacker’s attention but which become worthwhile targets because of their role as gateways to more valuable information.
Threats can be applied at various levels. Communications to and from a device can be subject to sniffing of sensitive data, such as passwords, direct remote attacks via backdoors, and indirect attacks through remote nodes. Software, in turn, can contain malware such as viruses and rootkits, exploit buffer and/or stack overflows, or tamper with privilege levels to give unauthorized users greater powers to explore and control a system than they should have.
It’s important to understand and protect against these sorts of attacks. However, it could be argued that they are less important than attacks against the underlying hardware of a system. Hardware can be attacked through non-invasive means such as illicit access to debug ports or side-channel analysis, and through invasive means such as decapsulation and direct probing. Once the hardware is compromised, all bets are off.
The security issue is becoming more acute as embedded devices, such as those being developed to become part of the Internet of Things, start using embedded SIMs (eSIM or eUICC) to provide what are presumed to be secure identities. As system developers increase the level of trust they attribute to such devices, the value of the devices as hacking targets increases.
SoC designers are, by now, well-versed in fighting the war of escalation between those with secrets to protect (either locally-held information or potential access to other systems) and hackers who want to exploit security vulnerabilities for gain.
For example, they’ll provide watchdog timers to protect a chip against efforts to learn about its function by tampering with its operation. They’ll lock down debug ports, so they aren’t open to all-comers for exploitation. They’ll obfuscate how much time and power it takes to run each instruction, so that hackers can’t learn anything about the device’s operation from analyzing these profiles. They’ll perform integrity checking on data and instruction paths to negate attacks using fault injection. And so on.
Synopsys has been developing secure IP incorporating many of these preventive measures for a while now, and its latest release is a pre-verified DesignWare ARC Secure IP Subsystem, which provides a combination of trusted hardware modules and a supporting software environment.
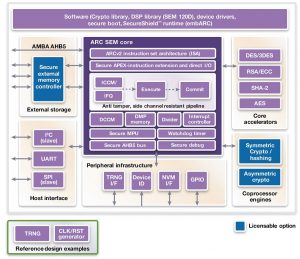
It is based around either a DesignWare ARC SEM110 or an SEM120D Security Processor with SecureShield technology, which enables the creation of a Trusted Execution Environment (TEE) for secure code execution, secure handling of assets, and tamper protection. The ARC SEM processors also have side-channel protection; a tamper-resistant pipeline with inline address scrambling; error detection and parity checking on memories; and secure debug to protect against theft of keys, code or other sensitive information.
The Secure IP Subsystem has secure instruction- and data-memory controllers that enable code or data to be stored in encrypted form outside the Secure Subsystem, and then decrypted on the fly as the processor fetches it from memory.
Figure 1 The DesignWare ARC Secure IP Subsystem (Source: Synopsys)
Cryptography options include dedicated hardware cryptography engines, to handle typical ciphers, and hashing algorithms such as AES, DES/3DES, SHA-256, RSA and ECC. The ARC Secure IP Subsystem also includes access to the DesignWare Cryptography Software Library, which has been validated by NIST.
Software and development support includes a variety of tools to enable the creation of secure systems. In addition to the crypto library, the ARC Secure Subsystem software offering includes secure boot, the SecureShield runtime library, hardware abstraction layer and device drivers. Provisioning tools include a secure boot toolkit, and a tool for creating firmware that can work with the secure external memory controller. Synopsys has worked with third-party and open-source software to provide a complete embedded SIM solution. This includes JavaCard OS, the eSIM stack, and the embARC open software platform.
Further information
- Learn more about DesignWare ARC Subsystems
- Learn more about ARC SEM Processors and SecureShield technology
- Learn more about Synopsys DesignWare Security IP Solutions
Author
Rich Collins is product marketing manager, IP subsystems, Synopsys.
 Rich Collins is product marketing manager for IP subsystems at Synopsys
Rich Collins is product marketing manager for IP subsystems at Synopsys