Taking your first steps in leveraging the RISC-V toolchain
In the nine years since the initial public release of its open-source microprocessor instruction set architecture (ISA), RISC-V has grown from an academic innovation into a mainstream choice for a wide variety of embedded applications. Semico Research estimates that by 2025 over 62 billion RISC-V-based devices will ship globally 1. As more RISC-V intellectual property (IP) becomes available and new silicon and development boards reach entry-level designers, we need to look at the state of the tools and consider how embedded developers make best use of RISC-V toolchain-based applications.
RISC-V International is a non-profit organization that was established in 2015 as The RISC-V Foundation to promote the technology. It aims to build upon the growing community of contributors, formalize the ISA and place it and other support in the public domain (via GitHub). The architecture is royalty-free not just for research, education, or prototyping, but also for production. There is no fee to use the ISA, no matter how often users download it nor the number of projects or products on which it is used. RISC-V International’s user community can vote and approve updates to the ISA via extensions.
The RISC-V advantage
RISC-V is a potential game changer for microcontroller and microprocessors. Embedded designers now have a choice for basing their products either on one of the proprietary commercial processor architectures, or using the royalty-free open architecture. In many industrial markets where the number of processors in a production series can number in the millions, the cost savings just from eliminating royalty fees can be substantial. Several disk drive vendors and automotive companies have already invested heavily in RISC-V designs.
The advantages go beyond cost. Defense and aerospace designers have historically experienced project delays because of extra needs to negotiate non-disclosure agreements (NDAs) and additional fees so that they can modify a proprietary ISA for specialized applications. Or they have been forced to develop their own architectures from scratch. These and other similarly challenged developers can now download the well-documented open-source RISC-V ISA for free, and perform any necessary modifications far more freely. The open license explicitly specifies that users can modify the ISA at will, with no obligation to upload or publish their modifications, so companies can keep their modified RISC-V-based ISA proprietary.
The RISC-V architecture
RISC-V is a processing architecture, not a processor implementation. Its original creators at The University of California – Berkeley avoided any bias towards a particular microarchitecture or silicon technology with the ISA. It can be implemented in an ASIC or FPGA, and on any process node. The first processor implementations by the Berkeley team were in the open-source Chisel hardware description language, and have been posted publically for anyone’s use. Since then, the number of silicon vendors offering RISC-V-based hardware has grown rapidly and continues to do so. As of today, about 100 hardware implementations are listed on RISC-V International’s website.
The architecture is modular, starting from the base specification that supports 32 and 64-bit integer. 128-bit mode integer is also defined, but intentionally left open as more designs become available using these denser memory maps. The base ISA is broken into two volumes: the User-Level Architecture (Volume I), and the Privileged Architecture (Volume II). The Privileged Architecture is designed for isolation of software stack components from the user portion of the operating system and application code.
Starting from a base ISA and then adding the necessary extensions like single-precision, double-precision, and quad-precision floating point, packed-SIMD instructions, or virtualization support, RISC-V can address a variety of system models from small footprint needs to multi-processor applications and on, eventually, DSP applications using SIMD.
RISC-V-based toolchain considerations for commercial products
Embedded RISC-V processor IP is showing up in new products, enabling software developers to port application code, a key requirement. The compiler, libraries, linker and debugger tool set to convert application source code to binary code to get it running on target hardware collectively comprise a toolchain. Toolchains integrated into an application development suite to support a specific product are known as a Software Development Kit (SDK)
Two open source compiler framework projects provide a partial solution to the RISC-V toolchain requirement: the GCC (GNU Compiler Collection) project and the newer LLVM project.
The GCC is an open source initiative providing compiler support for many RISC-V standard ISA variants. GCC also supports Linux and bare-metal (RTOS and no operating system) targets. GCC versions 7.1 and higher include RISC-V support.
The LLVM project open source compiler framework initiative also provides compiler backend and library support for RISC-V standard ISA variants. While the LLVM project has focused on Linux target operating system support, there is growing interest to extend support for embedded bare-metal target devices. LLVM versions 9.0.0 and higher include RISC-V support.
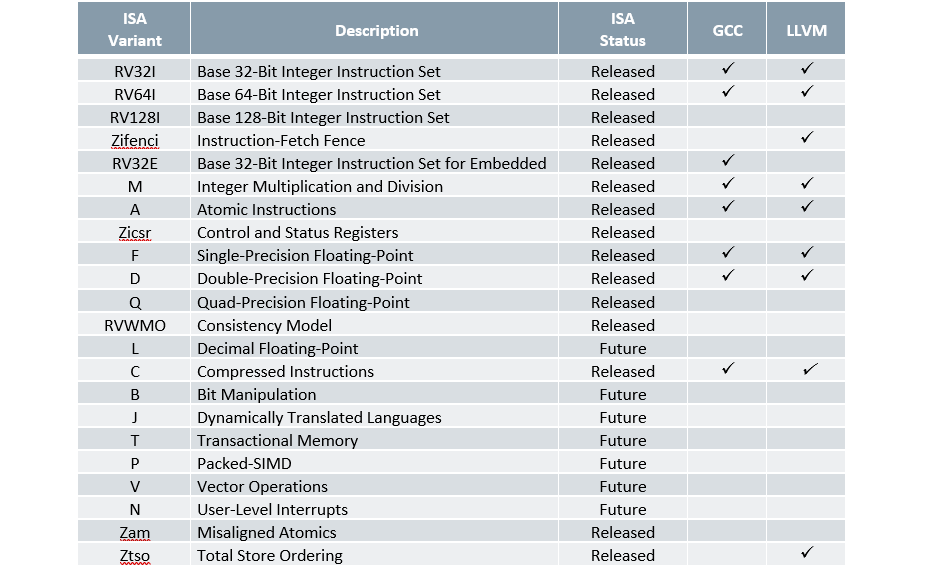
RISC-V variants supported by CGG and LLVM are shown in Table 1.
While software developers targeting RISC-V devices can download GCC or LLVM source code directly from the projects’ public open source repositories, this may not be an efficient first step in porting application software to a processor. Building and validating an open source-based toolchain is complex and fraught with many potential pitfalls, especially for those new to building their own toolchains. This white paper delves further into this topic. It addressed toolchain commercialization, customization and support toward the goal of confident deployment for RISC-V-based product development: “Ensuring the success of your RISC-V product with a commercial-grade software development ecosystem”.
 Pete Decher is the director of Sourcery Tools for the embedded division of Mentor, a Siemens Business. During 15 years at the company, he has been a senior product manager and business development manager. Previously, Decher was VP Engineering at Analogy, VP of Engineering at Teseda Corp. and Octavian Scientific, respectively. He holds an MSEE from Stanford University and a BSEE from Georgia Institute of Technology.
Pete Decher is the director of Sourcery Tools for the embedded division of Mentor, a Siemens Business. During 15 years at the company, he has been a senior product manager and business development manager. Previously, Decher was VP Engineering at Analogy, VP of Engineering at Teseda Corp. and Octavian Scientific, respectively. He holds an MSEE from Stanford University and a BSEE from Georgia Institute of Technology.