Protecting content transmitted over USB Type-C connections
The rapidly improving fidelity of video formats, such as 4K Ultra-High Definition (UHD), High Dynamic Range (HDR) and 8K UHD, is making it increasingly attractive to make unauthorized copies of such content – since consumers will pay more for higher quality, even from pirated sources.
The content industry relies on the High-bandwidth Digital Content Protection (HDCP) 2.2 security specification to protect such content from unauthorized copying or distribution. HDCP 2.2 is already widely used on HDMI connections, and on some DisplayPort connections, but rarely over legacy USB connections. However, as USB Type-C connections become increasingly popular, system-on-chip (SoC) developers will have to implement HDCP 2.2 so that the target devices will be able to play protected content over this latest iteration of USB.
Securing content
Organizations such as MovieLabs, founded by Hollywood studios Disney, Paramount, Twentieth Century Fox, Sony Pictures, Universal and Warner Bros., provide guidelines on protecting their content on its journey from the source to the end displays. The MovieLabs Enhanced Content Protection specification says that devices that receive high-value content must implement strict security measures against copying or redistribution. The MovieLabs specification requires:
- Protection of content sent to a remote display using HDCP 2.2 link protection
- A hardware root of trust to protect Digital Rights Management and link-protection keys
- A secure computation environment, enforced by hardware, for authenticating code that performs critical operations at power-up and during runtime
- A protected video-processing pipeline
- A random number generator compliant with the NIST SP800-90C specification
It’s expensive to develop the in-house facilities to meet these requirements and easy to get it wrong, leaving an implementation vulnerable to attacks and the implementers open to potential liabilities.
For example, solutions based on a Trusted Execution Environment, enabled by a single CPU with hardware separation, may not be sufficient to ward off current or future attacks. Having the solutions contained in a dedicated embedded security module with a hardware root of trust helps address new threats in the field, and provides high-grade security protection to meet the strict robustness rules of the HDCP 2.2 specification. Fault detection and side-channel attack resistance must also be addressed as part of the solution, adding to the growing set of requirements.
Finding the right USB Type-C security solution
The introduction of the USB Type-C connector is making USB Type-C ubiquitous. The connector is small, reversible and can be used at both the host and device ends of a cable. It can simultaneously deliver power, data, video, and audio signals. Proprietary designs for USB video and HDCP over USB already exist and have been challenging to implement. Fortunately, DisplayPort Alternate Mode re-purposes USB Type-C pins for native DisplayPort signaling, making it possible to use existing HDCP solutions.
SoC developers who want to use USB Type-C to carry protected content can develop their own approach, although it will need to be well tested and certified to deliver the protections demanded by groups such as MovieLabs. Alternatively, designers can turn to a third party for IP that supports HDCP 2.2 over USB Type-C. If you choose this route you should ask potential suppliers:
- Are all the features required by the market supported in their solutions?
- How was this solution tested for interoperability?
- Is the solution certified by the Digital Content Protection licensing authority?
- Can you explain how robustness criteria were met?
- What protection is provided against side-channel attacks, code modifications, fuzzing, glitching and fault injection? How have those been evaluated and what were the results?
- How many designs and devices in the market use this implementation?
These questions are important because the robustness requirements are increasingly demanding and yet the specifications are open-ended with respect to resisting attacks, so you need to choose a supplier that understands how the challenges to content-protection schemes will escalate.
Protecting against future threats
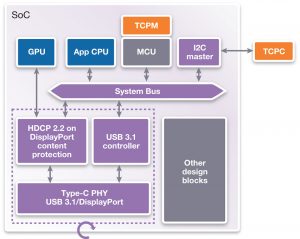
SoC developers must also ask potential suppliers to present their track records of successful, interoperable and secure solutions – and their plans to address future threats. Suppliers should offer a complete, robust and tested solution that meets the requirements of the relevant standards, which can also be adapted to meet new challenges. (Figure 1).
Figure 1 Complete DesignWare USB Type-C and HDCP 2.2 embedded security module (Source: Synopsys)
Synopsys offers a certified and interoperable solution that enables the highest content protection over the USB Type-C interface for UHD multimedia SoCs. The DesignWare HDCP 2.2 Embedded Security Module can support the authentication, key exchange, and secure key-stream generation facilities necessary to meet the HDCP 2.2 on DisplayPort specification.
DesignWare USB-C IP solutions, including controllers, PHYs, VIP, IP Subsystems and IP Prototyping Kits are also available. Combined, these IP offerings enable content protection over the USB Type-C interface.
Author
Dana Neustadter is a senior manager of product marketing for Synopsys’ Security IP solutions. Neustadter has over 20 years of diversified experience in the security, IP, semiconductor and EDA industries. Prior to joining Synopsys, Dana held multiple senior leadership roles, including director of product management and board director at Elliptic Technologies, responsible for the strategic vision and marketing of security IP. Neustadter has also had leadership and engineering roles at Mitel Semiconductor, Chrisalis-ITS and Silicon Access Networks. She holds a Masters and Bachelor degree in electrical engineering.